Modern malware and botnet C2 protocols use TLS encryption in order to blend in with "normal" web traffic, sometimes even using legitimate services likeTwitter orInstagram.
I did a live demo at the CS3Sthlm conference last year, titled "TLS Interception and Decryption", where I showed how TLS interception can be used to decrypt and analyze malicious HTTPS network traffic. During the demo I used DNS-over-HTTPS (DoH) and posted messages to Pastebin and Twitter, pretending to be a malware or malicious actor. The HTTPS network traffic was decrypted and analyzed live as part of my demo. The CS3Sthlm organizers have posted a video recording of the live demo on YouTube.

Image: Erik demoing TLS Interception and Decryption at CS3Sthlm 2019
We are now releasing a PCAP file with the decrypted network traffic captured during this live demo here:
» https://www.netresec.com/files/proxy-191023-091924.pcap«
This blog post provides a step-by-step walk-through of the decrypted HTTPS traffic in the released capture file.
The TLS decryption was performed by connecting a laptop to a custom WiFi access point,
which was a Raspberry Pi configured as in our
"Raspberry Pi WiFi Access Point with TLS Inspection"
blog post.
I additionally enabled the
PCAP-over-IP feature in PolarProxy
by starting it with the
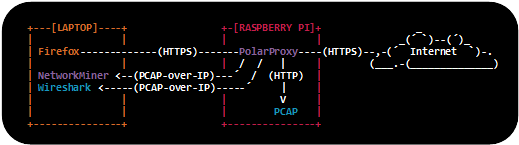
Image: Live demo network with Laptop (Browser, NetworkMiner, Wireshark), Raspberry Pi (PolarProxy) and the Internet.
Below follows a breakdown of various significant events of my demo and where you can find these events in the released capture file.
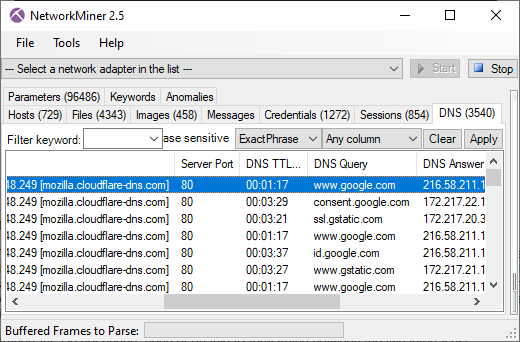
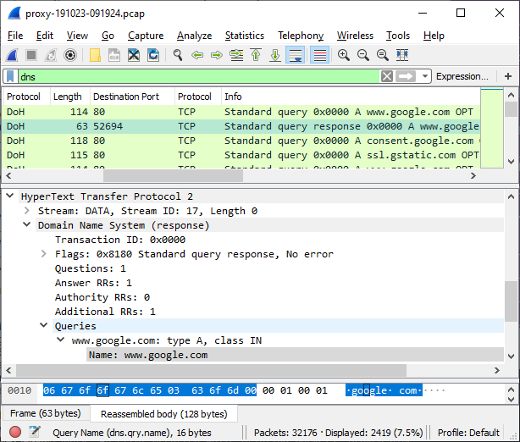
DNS lookup of "www.google.com" using DoH
- Frame: 833
- Protocol: DoH using HTTP/2 POST
- Five tuple: 192.168.4.20:52694 104.16.248.249:80 TCP
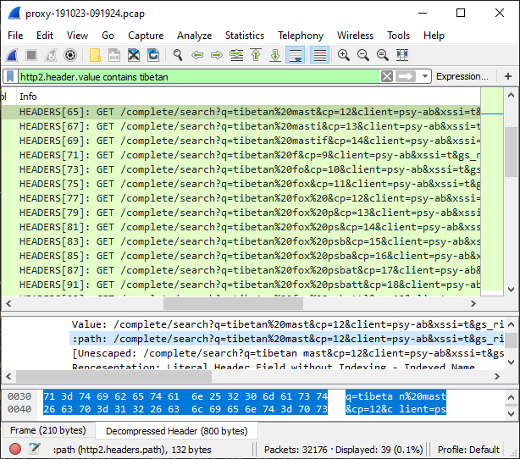
Google search for "tibetan fox psbattle"
- Frame: 2292
- Protocol: HTTP/2
- Five tuple: 192.168.4.20:52716 216.58.211.4:80 TCP
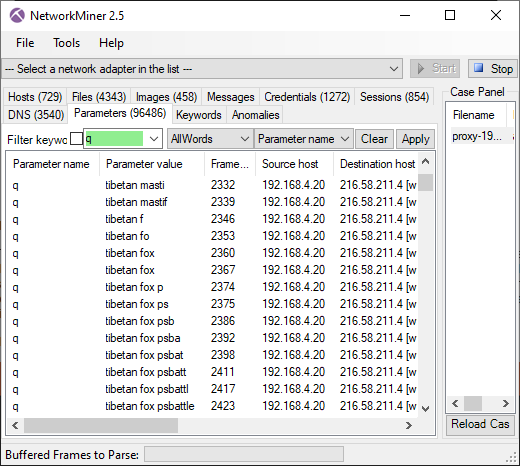
Tibetan Fox image downloaded from reddit
- Frame: 3457
- Protocol: HTTP/2
- Five tuple: 192.168.4.20:52728 151.101.85.140:80 TCP
Orginal "tibetan fox" image downloaded from this reddit thread.
Tibetan Fox Remix Image HTTP/2 Download
- Frame: 5805
- Protocol: HTTP/2
- Five tuple: 192.168.4.20:52769 151.101.84.193:80 TCP
DNS Lookup of "cs3sthlm.se"
- Frame: 13494
- Protocol: DoH using HTTP/2 POST
- Five tuple: 192.168.4.20:52699 104.16.249.249:80 TCP
Images downloaded from CS3Sthlm's website
- Frame: 14134
- Protocol: HTTP/1.1
- Five tuple: 192.168.4.20:52896 192.195.142.160:80 TCP
Data sent in HTTP/2 POST to Pastebin
- Frame: 18572
- Protocol: HTTP/2 POST
- Five tuple: 192.168.4.20:52904 104.22.2.84:80 TCP
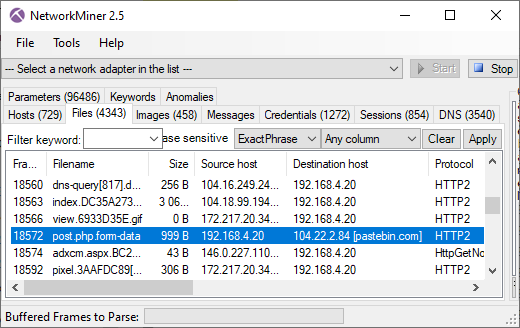
The file "post.php.form-data" contains the data sent to Pastebin in the HTTP/2 POST request. Here are the reassembled contents of that file, including the "hello cs3 I am a malware" message:
Content-Disposition: form-data; name="csrf_token_post"
MTU3MTgyMjg5OTFwcjBzODJaQ0NuUk9PT1B3ZTl0b20zdFg3ZkhXQ1R4
-----------------------------54168074520069581482009826076
Content-Disposition: form-data; name="submit_hidden"
submit_hidden
-----------------------------54168074520069581482009826076
Content-Disposition: form-data; name="paste_code"
hello cs3 I am a malware
-----------------------------54168074520069581482009826076
Content-Disposition: form-data; name="paste_format"
1
-----------------------------54168074520069581482009826076
Content-Disposition: form-data; name="paste_expire_date"
1H
-----------------------------54168074520069581482009826076
Content-Disposition: form-data; name="paste_private"
0
-----------------------------54168074520069581482009826076
Content-Disposition: form-data; name="paste_name"
malware traffic
-----------------------------54168074520069581482009826076--
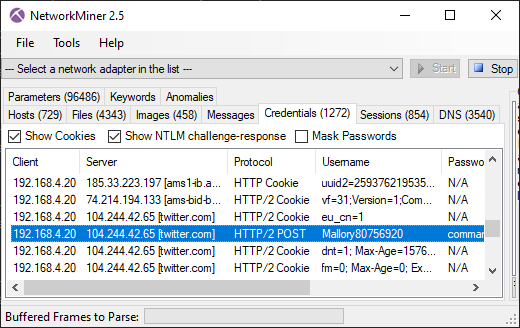
Mallory80756920 logs in to Twitter
- Frame: 24881
- Protocol: HTTP/2 POST
- Five tuple: 192.168.4.20:53210 104.244.42.65:80 TCP
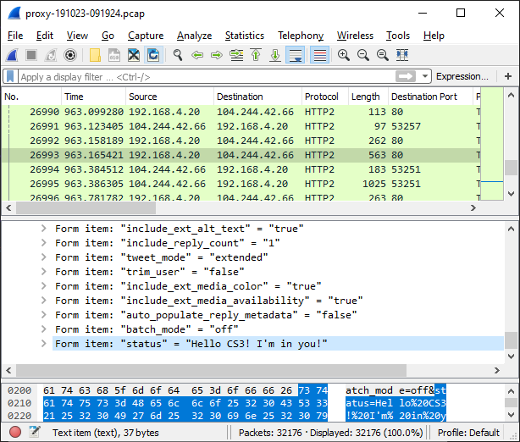
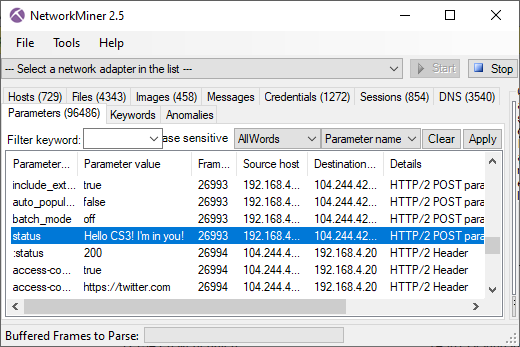
Mallory80756920 posts a Tweet
- Frame: 26993
- Protocol: HTTP/2 POST
- Five tuple: 192.168.4.20:53251 104.244.42.66:80 TCP
Mallory80756920 tweeted "Hello CS3! I'm in you!". The data was sent to twitter using an HTTP/2 POST request.
Conclusions
A great deal of the interesting TLS traffic in the analyzed capture file is using the HTTP/2 protocol. This doesn't come as a surprise since more than half of all HTTPS traffic is using HTTP/2 nowadays (sources: server protocol statistics,client protocol statistics). It is therefore essential to be able to analyze HTTP/2 traffic if you have a TLS inspection (TLSI) solution in place. Unfortunately many TLSI products don't yet support the HTTP/2 protocol.
Wireshark was one of the first network traffic analysis tools to implement HTTP/2 support, much thanks to Alexis La Goutte. However, Wireshark's excellent "File > Export Objects" doesn't yet support extraction of files from HTTP/2 traffic. There are other ways to extract HTTP/2 file transfers with Wireshark, but they require a few additional steps in order to carve out the file to disk.
Luckily NetworkMiner extracts files from HTTP/2 as of version 2.5. In fact, we believe NetworkMiner is the first open source tool to support automatic HTTP/2 file extraction from PCAP.
Finally, I'd like to stress the point that modern malware use HTTPS, so you need to have a TLSI solution in place to analyze the malicious traffic. As the majority of all HTTPS traffic is using HTTP/2 you also need to ensure that you're able to analyze HTTP/2 traffic passing through your TLSI solution.
 Share on Facebook
Share on Facebook  Tweet
Tweet  Submit to reddit.com
Submit to reddit.com